Stories
Listing
-
Investigating Environmental Crimes: The Huntington Oil Spill
April 22, 2024
The FBI and partners used groundbreaking techniques and advanced technology to investigate the 2021 disaster.
-
FBI Launches Trauma Notification Training
April 22, 2024
The FBI has launched an updated, mobile-friendly Trauma Notification Training program to help ensure trauma notifications are delivered with professionalism, dignity, and compassion.
-
Wray: Chinese Government Poses 'Broad and Unrelenting' Threat to U.S. Critical Infrastructure
April 18, 2024
FBI Director Christopher Wray warned national security and intelligence experts that the risks posed by the government of China to U.S. national and economic security are “upon us now."
-
'A Great Partner in the Community'
April 17, 2024
An Oklahoma City area pastor who had a run-in with the FBI in the late ’90s is set to be honored by the Director and special agent who once pursued him.
-
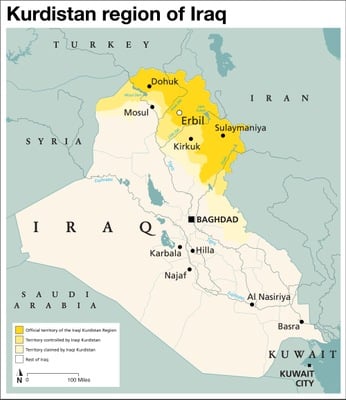
April 15, 2024
A U. S. Army veteran who established an illegal weapons facility in the Kurdistan region of Iraq— and who proceeded to both direct and engage in the torture of one of his employees—has been sentenced to 70 years in federal prison for those crimes and for additional crimes linked to his role at the facility.
-
Director Addresses Birmingham Civil Rights Conference
April 15, 2024
FBI Director Christopher Wray summoned the words of civil rights leader Dr. Martin Luther King Jr. in a speech in Alabama encouraging civil rights activists and law enforcement leaders to forge ahead in their fight for justice despite the persistence of violent, bias-motivated hate crimes.
-
Protecting Quantum Science and Technology
April 12, 2024
Foreign adversaries are increasingly targeting a wide range of U.S. quantum companies, universities, and government labs. The National Counterintelligence Task Force's Quantum Information Science Counterintelligence Protection Team unites the FBI with our intelligence and security partners to protect quantum information science and technology developed in the U.S. and like-minded nations.
-
Historic Firearms Returned to Philadelphia Museum
April 10, 2024
The FBI and our partners recently helped recover stolen Revolutionary War-era U.S. firearms that were a part of a string of thefts in the 1960s and 1970s in Pennsylvania.
-
April 9, 2024
Such a requirement would hinder the Bureau's ability to obtain and act upon threat intelligence and—by extension—to prevent potential terrorist or cyber-facilitated attacks against the homeland, Director Christopher Wray said on April 9.
-
FBI Countering Cyber Threats Through ‘Joint, Sequenced Operations,’ Director Says
April 4, 2024
FBI Director Christopher Wray described the Bureau’s aggressive efforts to counter cyber threats and go after attackers in an April 4 speech at a conference of leading cybersecurity experts.
-
NICS Enhanced Background Checks for Under-21 Gun Buyers Showing Results
March 25, 2024
A 2022 law requires the FBI's National Instant Criminal Background Check System analysts to go beyond the routine when requests are for prospective gun buyers under 21.
-
Investigations and Oversight: Director Wray Discusses FBI’s Commitment to Government Accountability
March 19, 2024
The FBI pursues the cause of government accountability by investigating abuses of power by law enforcement officers and the corruption of public officials, and by holding our own workforce to a higher standard, FBI Director Christopher Wray said during the University of Georgia’s 2024 Getzen Lecture on Government Accountability on March 19.
-
FBI Boston Recovers and Returns 22 Historic Artifacts to Okinawa, Japan
March 15, 2024
The Boston Division recovered 22 historic artifacts looted at the end of World War II and has orchestrated their return to Okinawa Prefecture in Japan.
-
FBI Jacksonville Program Aims to Keep Connected Kids Safe
March 7, 2024
FBI Jacksonville's Be Smart With Your Kids' Smartphone program partners with local law enforcement and schools to keep connected kids safe.
-
A Proven Partnership: Director Discusses FBI-Military Collaboration at West Point
March 4, 2024
On March 4, FBI Director Christopher Wray visited the U.S. Military Academy at West Point to speak with future U.S. Army officers about the Bureau’s legacy of collaboration with the Defense Department.
-
FBI Hockey Team Battles Secret Service in Triple-Overtime Thriller
March 4, 2024
In an electrifying and hard-fought game, the FBI lost 3-2 in triple overtime to its longtime hockey rivals the U.S. Secret Service. The sold-out charity game raised about $35,000 to benefit the families of law enforcement officers and first responders killed in the line of duty.
-
Director Outlines New Intelligence Program Strategy
February 29, 2024
FBI Director Christopher Wray today outlined the Bureau’s new intelligence program strategy and emphasized how partnerships, collaboration, and innovation are essential to combatting emerging national security threats.
-
Kansas City Man Sentenced to Life in Prison for Cyberstalking, Murder
February 23, 2024
A convicted felon received a life sentence for using a GPS device to track the vehicle of a man he later murdered. It's a case that marked the first filing of both the cyberstalking and the cyberstalking resulting in death charges in the Western District of Missouri.
-
Director Wray Talks Partnerships with Sheriffs
February 15, 2024
FBI Director Christopher Wray met with the Major County Sheriffs of America during their 2024 Winter Conference on February 9 in Washington, D.C., to discuss threats facing law enforcement and strategies to address them.
-
FBI Recruitment Supports NSM-3
February 13, 2024
The FBI supports the same goals as the NSM-3 initiative—outlined in a 2021 White House memorandum—to strengthen and grow our national security and foreign policy workforce.
-
February 8, 2024
Get a behind-the-scenes look at the FBI's role in ensuring safety at the Super Bowl.
-
International Drug Trafficking Organizations Takedown
February 6, 2024
A team of FBI and international law enforcement agencies conducted multiple takedowns the morning of January 30, 2024, across the United States, and Canada to disrupt and dismantle an international organized crime syndicate importing and exporting massive quantities of drugs across the North American continent.
-
China's Hackers Have Entire Nation in Their Crosshairs, FBI Director Warns
January 31, 2024
Chinese government hacking efforts now target the entire American populace, and the escalating urgency of the overall threat that China poses to U.S. national security requires more investment in the FBI’s capabilities, FBI Director Wray warned lawmakers during a January 31 appearance before the House Select Committee on the Strategic Competition Between the United States and the Chinese Communist Party.
-
How FBI New York Helps Protect New Year’s Eve
January 31, 2024
Each year, the FBI’s New York Field Office joins forces with local, state, and federal partners to ensure that residents and visiting tourists can safely partake in New Year’s Eve celebrations across the city.
-
January 30, 2024
A basketball game between high-schoolers and the FBI sought to improve relations between the Bureau's Washington Field Office and the communities it serves and to show the students a possible future.
-
Missing Person Alert: Help the FBI Find Liam Biran
January 23, 2024
A wine blogger and travel enthusiast from New Jersey who disappeared during a 2019 trip and hasn’t been seen since has prompted the FBI to seek the public’s help finding him.
-
The Financially Motivated Sextortion Threat
January 16, 2024
The FBI this week issued a new warning about an evolving online threat targeting minors and young adults: financially motivated sextortion.
-
FBI, NSA Leaders Talk Election Security, Power of Collaboration at Fordham ICCS
January 9, 2024
FBI Director Christopher Wray on January 9 said the Bureau is well-postured to defend against foreign interference heading into the 2024 election cycle, despite the growing number of foreign actors and nation-states seeking to disrupt our democratic process.
-
January 8, 2024
The FBI seeks to bring closure in the 50-year-old case of Cathy Davidson, who was 6 years old when she was reported missing in Michigan, on September 1, 1973.
-
December 22, 2023
A look back at some of the FBI's accomplishments and challenges in 2023.
-
December 12, 2023
The FBI's SWAT program began in a handful of field offices in 1973 to better prepare agents for tactical responses. Today's modern SWAT is the largest tactical force in the country.
-
December 11, 2023
The Terrorist Screening Center began operating in December 2003 as a direct response to 9/11. Staffed by multiple U.S. government agencies, the TSC consolidated terrorism screening and created one federal terrorism watchlist.
-
FBI, HSI Investigation Leads to Historic War Crimes Indictment
December 6, 2023
The U.S. government on December 6 announced that it has brought its first-ever charges under the War Crimes Act of 1996 against four Russian-affiliated soldiers who allegedly violated the human rights of an American residing in Ukraine amid Russia’s full-scale invasion of the country.
-
FBI Underscores Commitment to Protecting American Jews, Muslims, Arabs Amid Israel-Hamas Conflict
December 6, 2023
The FBI is committed to fostering partnerships between the Bureau and the communities it serves and protects—in times of peace and crisis, alike.
-
FBI and HBCU Leaders Deepen Relationships at Baltimore Conference
November 28, 2023
The FBI and leaders of more than half of the country’s Historically Black Colleges and Universities (HBCUs) met in Baltimore to cultivate and nourish relationships as part of the ongoing Beacon Initiative.
-
The $9 Million Renewable Energy Ponzi Scheme
November 20, 2023
When Ray Brewer was looking to make a ton of money, he tapped into the renewable energy industry. From March 2014 through December 2019, Brewer ultimately stole more than $8 million from investors by claiming to build anaerobic digesters on dairies in California and Idaho.
-
Vitel’Homme Innocent Added to FBI’s Ten Most Wanted Fugitives List
November 15, 2023
The FBI, along with the U.S. Attorney’s Office for the District of Columbia and the U.S. Department of State, announced the addition of Vitel’Homme Innocent to its Ten Most Wanted Fugitives list. A reward of up to $2 million is being offered for information leading to his arrest and/or conviction.
-
Osage Discussion Spotlights Relationship Between FBI and Native Americans
October 23, 2023
The special agent in charge of the FBI’s Oklahoma City Field Office joined local Native American leaders and the author of a best-selling book about murders on the Osage Nation a century ago for a panel discussion in Oklahoma.
-
Update: FBI Helps Recover Nearly 200 Bodies from Colorado Funeral Home
October 20, 2023
On November 8, 2023, Jon Hallford and Carie Hallford, owners of Return to Nature Funeral Home were arrested on suspicion of committing crimes related to abuse of a corpse, felony, money laundering, and forgery.
-
FBI Director Convenes Five Eyes Summit on Protecting Innovation, Preventing Economic Espionage
October 18, 2023
During an October 17 fireside chat with intelligence chiefs from across the Five Eyes partnership, FBI Director Christopher Wray called the Chinese Communist Party the foremost threat to global innovation and suggested that partnerships are the best way to fight back.
1 - 40 of 1251 Results