International Business E-Mail Compromise Takedown
Multiple Countries Involved in Coordinated Law Enforcement Effort
Today, federal authorities—including the Department of Justice and the FBI—announced a major coordinated law enforcement effort to disrupt international business e-mail compromise (BEC) schemes that are designed to intercept and hijack wire transfers from businesses and individuals.
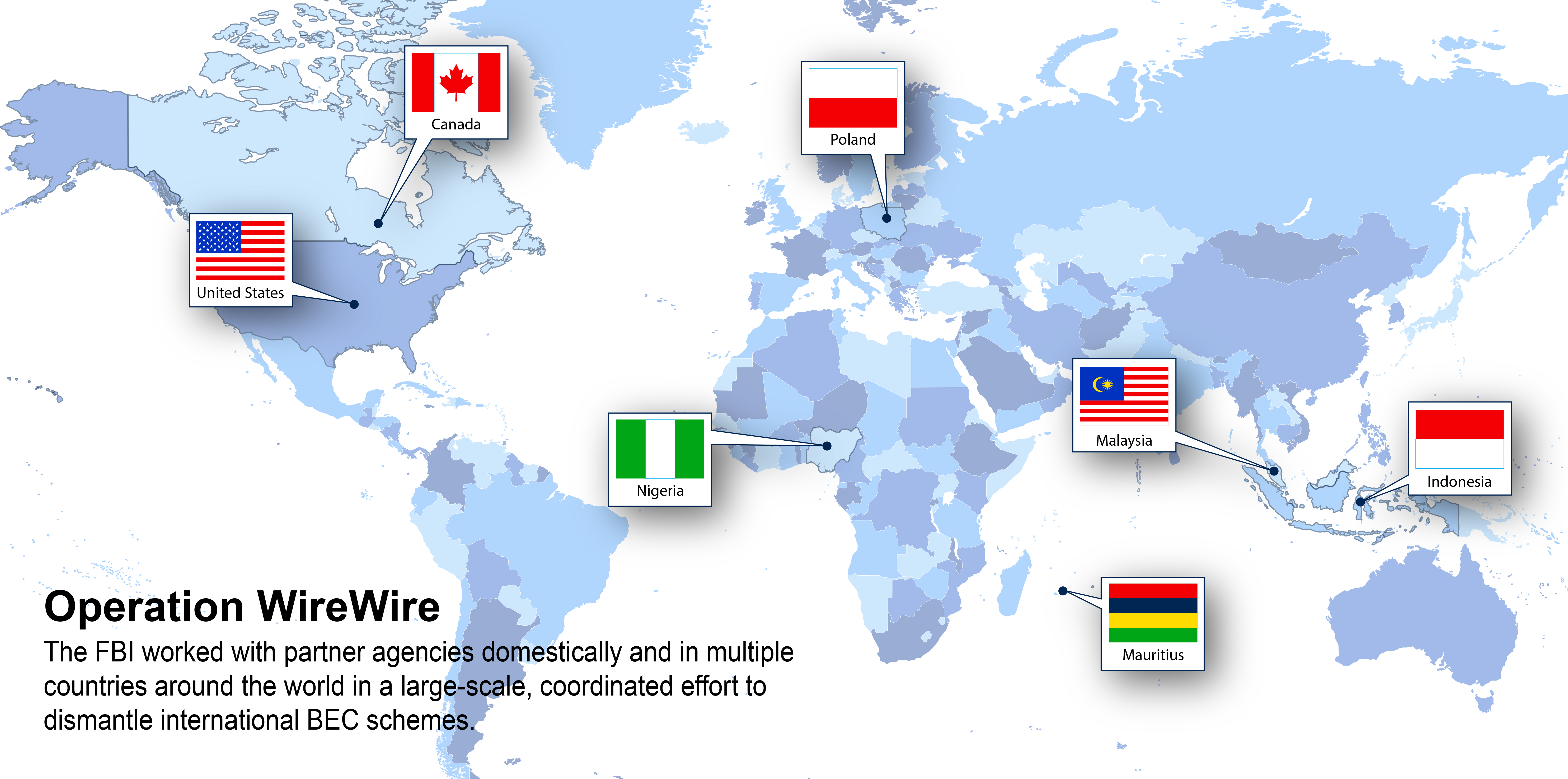
Operation WireWire—which also included the Department of Homeland Security, the Department of the Treasury, and the U.S. Postal Inspection Service—involved a six-month sweep that culminated in over two weeks of intensified law enforcement activity resulting in 74 arrests in the U.S. and overseas, including 42 in the U.S., 29 in Nigeria, and three in Canada, Mauritius, and Poland. The operation also resulted in the seizure of nearly $2.4 million and the disruption and recovery of approximately $14 million in fraudulent wire transfers.
A number of cases charged in this operation involved international criminal organizations that defrauded small- to large-sized businesses, while others involved individual victims who transferred high-dollar amounts or sensitive records in the course of business. The devastating impacts these cases have on victims and victim companies affect not only the individual business but also the global economy. Since the Internet Crime Complaint Center (IC3) began formally keeping track of BEC and its variant, e-mail account compromise (EAC), there has been a loss of over $3.7 billion reported to the IC3.
BEC, also known as cyber-enabled financial fraud, is a sophisticated scam that often targets employees with access to company finances and trick them—using a variety of methods like social engineering and computer intrusions—into making wire transfers to bank accounts thought to belong to trusted partners but instead belong to accounts controlled by the criminals themselves. And these same criminal organizations that perpetrate BEC schemes also exploit individual victims—often real estate purchasers, the elderly, and others—by convincing them to make wire transfers to bank accounts controlled by the criminals.
Foreign citizens perpetrate many of these schemes, which originated in Nigeria but have spread throughout the world.
During Operation WireWire, U.S. law enforcement agents executed more than 51 domestic actions, including search warrants, asset seizure warrants, and money mule warning letters. And local and state law enforcement partners on FBI task forces across the country, with the assistance of multiple district attorney's offices, charged 15 alleged money mules for their roles in defrauding victims.
The role of money mules, witting or unwitting, in BEC schemes is very important—they are used to receive the stolen money and then transfer the funds as directed by the fraudsters. The mules usually keep a fraction of the money for their trouble.
“We will continue to work together with our law enforcement partners around the world to end these fraud schemes and protect the hard-earned assets of our citizens.”
FBI Director Christopher Wray
Today’s announcement highlighting this recent surge in law enforcement resources targeting BEC schemes “demonstrates the FBI's commitment to disrupt and dismantle criminal enterprises that target American citizens and their businesses,” according to FBI Director Christopher Wray.
And he added, “We will continue to work together with our law enforcement partners around the world to end these fraud schemes and protect the hard-earned assets of our citizens. The public we serve deserves nothing less.”
Awareness of BEC Schemes Can Safeguard Your Business
BEC schemes continue to evolve as criminals come up with new and inventive ways to scam businesses.
Here are the most current and frequent BEC scenarios identified by the FBI:
- Business Executive: Criminals spoof or compromise e-mail accounts of high-level business executives, including chief information officers and chief financial officers, which result in the processing of a wire transfer to a fraudulent account
- Real Estate Transactions: Criminal impersonate sellers, realtors, title companies, or law firms during a real estate transaction to ask the home buyer for funds to be sent to a fraudulent account
- Data and W-2 Theft: Criminals, using a compromised business executive’s e-mail account, send fraudulent requests for W-2 information or other personally identifiable information to an entity in an organization that routinely maintains that sort of information
- Supply Chain: Criminals send fraudulent requests to redirect funds during a pending business deal, transaction, or invoice payment to an account controlled by a money mule or bad actor
- Law Firms: Criminals find out about trust accounts or litigation and impersonate a law firm client to change the recipient bank information to a fraudulent account.
If you think you may have been victimized in a BEC scheme, please file a complaint with the IC3. The more information law enforcement has on these scams, the better equipped we’ll be to combat them.
And to further educate yourself on BEC schemes to help protect your business, read more about how BEC schemes work and how you can avoid being victimized. You can also take a look at this IC3 public service announcement on BEC schemes.