How Cyber Crime Group FIN7 Attacked and Stole Data from Hundreds of U.S. Companies
Background
Three high-ranking members of a sophisticated international cyber crime group operating out of Eastern Europe have been arrested and are currently in custody facing charges filed in U.S. District Court in Seattle. According to three federal indictments unsealed today, Ukrainian nationals Dmytro Fedorov, Fedir Hladyr, and Andrii Kopakov, are members of a prolific hacking group widely known as FIN7 (also referred to as the Carbanak Group and the Navigator Group, among other names). Since at least 2015, FIN7 members engaged in a highly sophisticated malware campaign targeting more than 100 U.S. companies, predominantly in the restaurant, gaming, and hospitality industries. As set forth in indictments unsealed today, FIN7 hacked into thousands of computer systems and stole millions of customer credit and debit card numbers as well as proprietary and non-public information, which the group used or sold for profit.
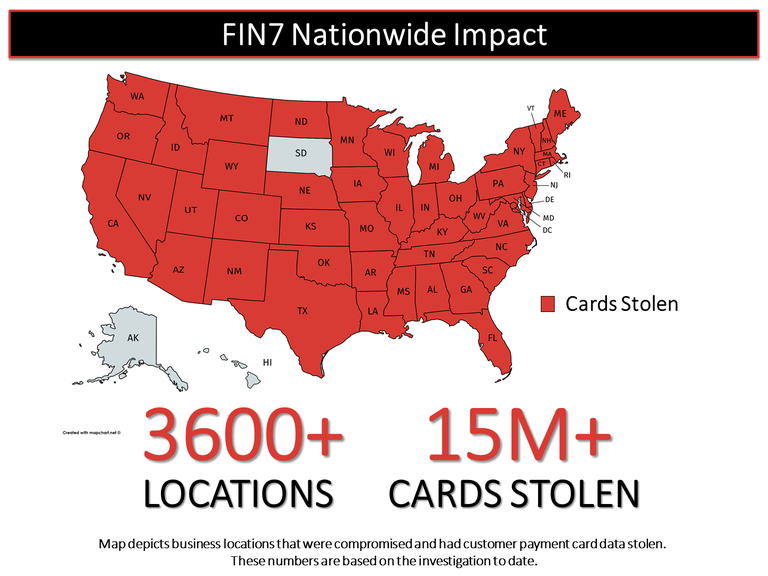
In the United States alone, FIN7 successfully breached the computer networks of companies in 47 states and the District of Columbia, stealing more than 15 million customer card records from over 6,500 individual point-of-sale terminals at more than 3,600 separate business locations. Additional intrusions occurred abroad, including in the United Kingdom, Australia, and France. Companies that have publicly disclosed hacks attributable to FIN7 include such familiar chains as Chipotle Mexican Grill, Chili’s, Arby’s, and Jason’s Deli. Additionally in Western Washington, FIN7 targeted the Emerald Queen Casino and other local businesses.
For more information, view the U.S. Attorney's Office, District of Western Washington press release.
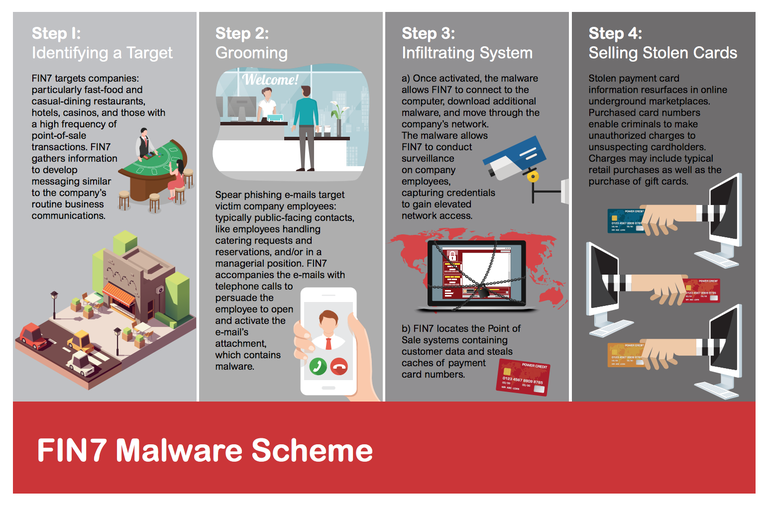
How FIN7 Attacked and Stole Data
Sophisticated Social Engineering: Phishing and Calling
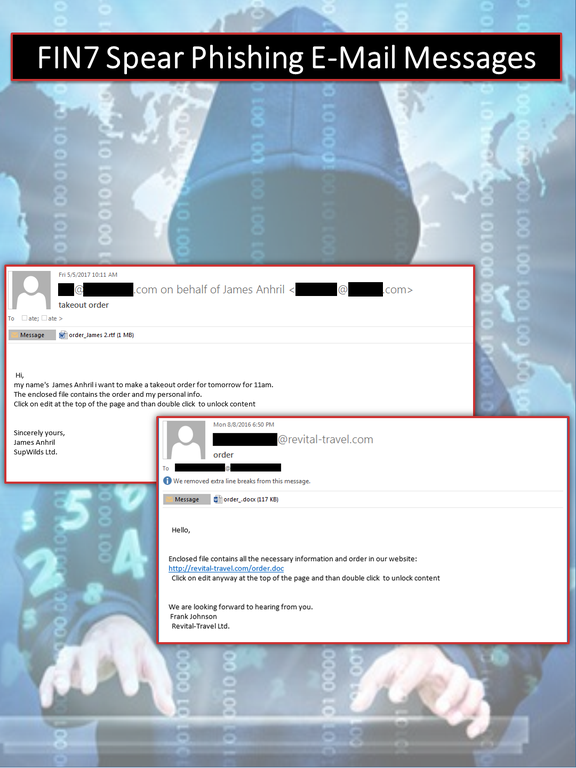
FIN7 typically initiated its cyber attacks by delivering a “phishing” email to a company employee. Each email included an attached file, often an innocuous-appearing Microsoft Word document, with embedded malware. The text within the email simulated a legitimate business-related message in order to lead the recipient employee to open the attachment and unwittingly activate the malware that would infect the computer. For example, when targeting a hotel chain, the sender of the phishing email might claim to be interested in making a reservation with details enclosed in the attachment. When targeting a restaurant, the phishing email might refer to placing a large catering order or voice a complaint about prior service or food quality, further described in an attachment.
In many cases, FIN7 would accompany the phishing emails with a telephone call to the victim company employee about the same topic, which was intended to legitimize the phishing email. The caller often directed the employee to the recently sent phishing email to further entice the employee to open the attached file and activate the malware.
Network Intrusion: Control and Data Exfiltration
Once infected, the compromised victim computer connected to one of FIN7’s command and control servers located throughout the world. Through a specially designed control panel, FIN7 could download a wide array of additional malware to the victim computer, remotely send commands and receive data, and move laterally through the company’s network. Among other tools, FIN7 incorporated and adapted the notorious Carbanak malware, which was used by other cybercriminals in a massive transnational attack on the banking industry. FIN7’s malware allowed its members to conduct surveillance on company employees, including taking screen shots and even video recordings of desktop activity, enabling them to secretly steal credentials and other network information. FIN7 then used its unauthorized access to the victim’s computer system to locate and extract various information and property of value, such as financial information and caches of customer payment card data.

FIN7 most commonly focused on fast-food and casual dining restaurants, hotels, casinos, and businesses with a high frequency of point-of-sale transactions, including businesses with dozens of locations operating in Western Washington. With these and other victims, FIN7 sought to steal credit, debit, and in some cases gift card data, used during legitimate customer purchases.

Selling Stolen Cards
Since 2015, FIN7 successfully stole data for more than 15 million payment cards, many of which have been offered for sale through online underground marketplaces for stolen data. The purchasers could then use the stolen card numbers to make unauthorized charges on accounts belonging to unsuspecting cardholders. Investigators have observed typical retail purchases as well as the purchase of gift cards.
Who is FIN7?
FIN7 is one of the most sophisticated and aggressive malware schemes in recent times, consisting of dozens of talented hackers located overseas. FIN7 uses an arsenal of constantly evolving malware tools and hacking techniques, and controls infected computers through a complex web of servers located throughout the world. The masterminds behind the criminal enterprise created a fake computer security business called Combi Security which they used to recruit new members and to add a thin veil of legitimacy to the hacking scheme. However, there was nothing legitimate about the scores of attacks FIN7 launched against over 100 unsuspecting victims.


